Router Threat Model
Introduction
To promote consistency across the industry, we have adopted the basic threat model described in section 2.3 of Germany's Federal Office for Information Security BSI TR-03148 'Secure Broadband Router - Requirements for secure Broadband Routers' (version 1.1, dated 30th April 2020).
Note that an attack may also originate from a visitor to the home or premises, such as a tradesperson, a colleague, a (child's) friend or a guest. If the visitor has malicious intentions then a major risk is that they gain administrator credentials printed on the router. However, visitors may also unintentionally introduce an attack path by connecting devices to the LAN or being given the Wi-Fi password.
Basic Threat Model
The BSI TR-03148 Threat Model is reproduced below:
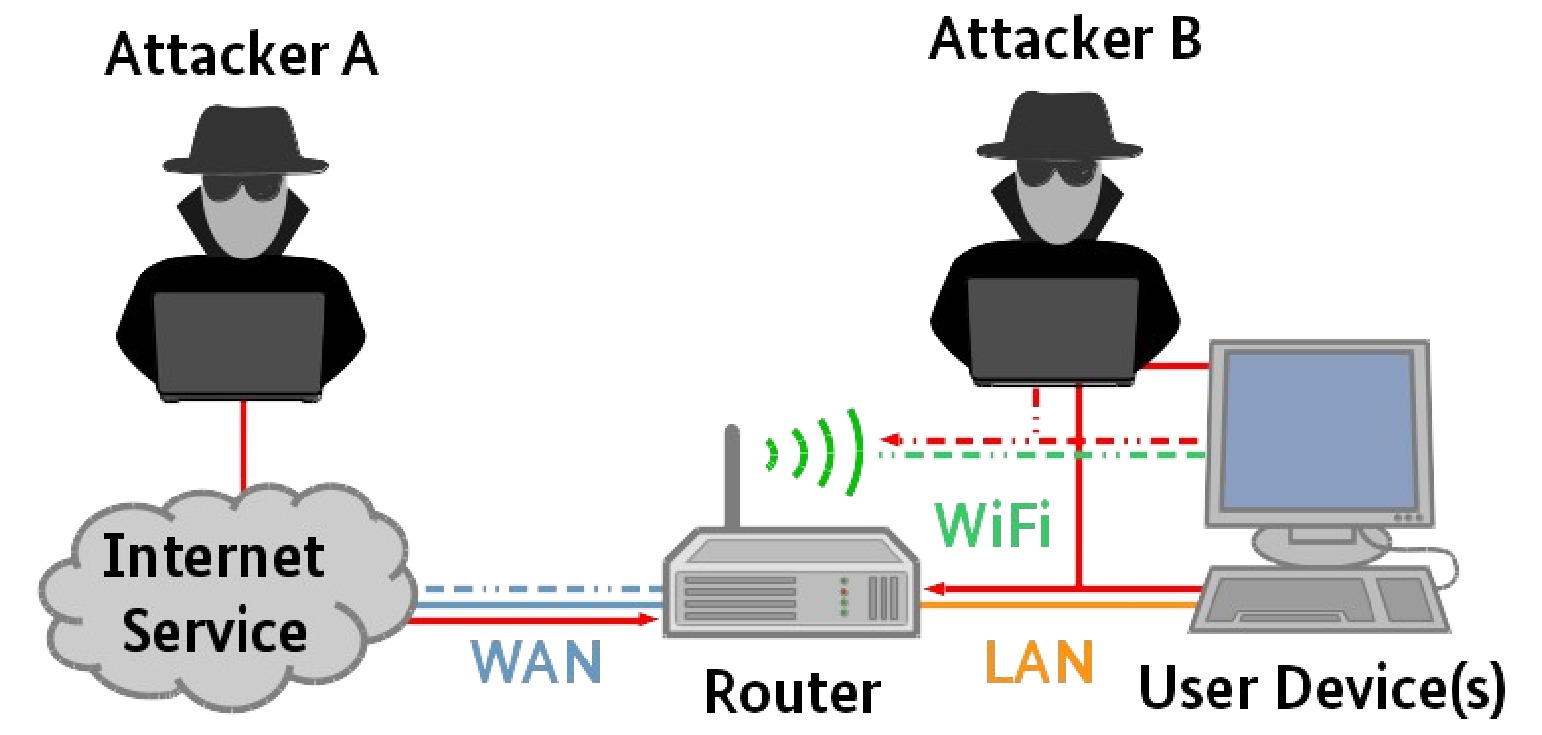
As stated in the introduction above, the person introducing the threat is not always obviously hostile and may be inadvertently connecting an infected or poorly configured device to the network.
Attacker A only has access to the router via the WAN interface, and only has as much information as is obtainable on the WAN interface of the router. Generally, the attacker would need to manipulate the router's functionalities in order to gain access to assets connected to the router over the LAN or WLAN (Wi-Fi). The goal of the attacker is to gain access to sensitive data, such as credentials of the end-user or devices.
Attacker B may being within range of the WLAN or have access to the LAN. As the approximate range of Wi-Fi is 70m indoors and 250m outdoors, WLAN coverage often extends well outside of the premises, especially if the attacker is using a directional aerial. Such an attack could be mounted from adjacent buildings, floors above or below the premises or even from vehicles or public areas in the vicinity. Additionally, with some routers offering additional longer-range communications, such as LoRaWAN, Bluetooth or mobile connections, the WLAN attack range can be significant, so increasing the need to make the interface secure (see Advanced Threat Model below). The attacker may also have access to a LAN connection. In this scenario, the goal of the attacker remains to gain access to sensitive data, but now the attacker additionally has access to other devices on the WLAN and LAN networks.
An extended scenario is where the attacker has access to the management functions of the router by gaining the credentials of the private network or compromising a device on the private network. This attack could be exploited by Attacker A through the WAN interface.
Unauthorised physical access to the router, especially where the administrator credentials are visible, could provide the attacker with full control of the router and greater opportunities to gain sensitive data and control of connected devices.
Advanced Threat Model
The basic threat model described above has been typical of many networks over the last 30 years. However, with the wide-spread adoption of smart devices both in the home and work environments, the threat environment has become considerably more complex. The diagram below, taken from the 'ManySecured: Securing the IOT Network with Collaborative Analytics' presentation, demonstrates a scenario which can often be found in homes, public offices and and business premises. The router may no longer be the only interface between the intranet and internet, as devices may have a variety of communications through which they communicate with services and other devices external to the intranet, such as mobile phone, LoRa and BlueTooth.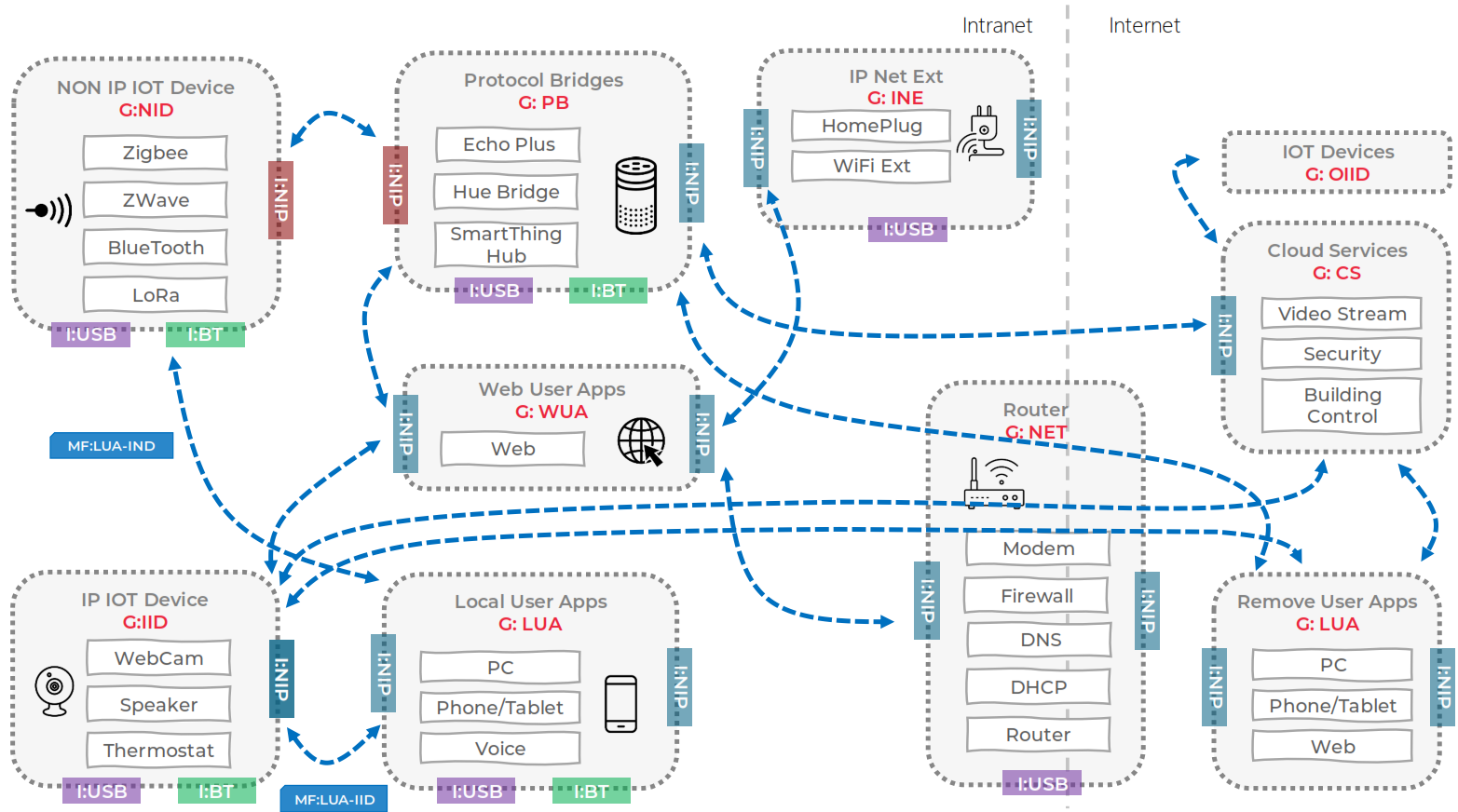
An in-depth description of the threats associated with such a network are presented in Essential Threats on Uni ed Taxonomy of the IoT Ecosystem.
Security Requirements of ManySecured Project were derived these threats facing networks that incorporate smart devices. The requirements include:
- Network requirements - secure device-to device connections,